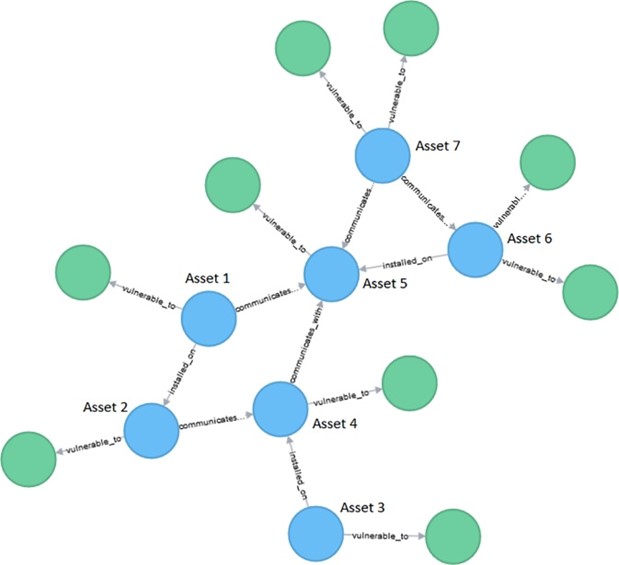
Ransomware in a supply chain environment.
In today’s world, the internet supply chain owners and participants need to make sure that not only their companies are secure from cyber-attacks, but the rest of the affiliates of the supply chain are secured as well. This need becomes more prominent with the rise in popularity of ransomware attacks...