FPGA technology and Supply Chain Cyber Security

CYRENE is a cutting-edge research project that focuses on the security, privacy, accountability, resilience and trustworthiness of Supply Chains. Securing Supply Chains is a difficult task as the cyberattacks are expected to quadruple each coming year according to the European Union Agency for Cyber Security (ENISA).
Hence, in order to counter new threats and protect complex environments from malicious actors, new systems and frameworks/approaches are needed. Hardware-based security, using Field-Programmable Gate Array (FGPA) technology, may provide a viable solution for securing critical parts of Supply Chain systems against cyberattacks.
What is an FPGA?
An FPGA is an Integrated Circuit (IC) silicon chip, which consists of Configurable Logic Blocks (CLBs) and a set of programmable interconnects. This chip allows hardware designers to connect blocks and configure them in order to perform everything, i.e., from simple logic processes to complex functions. The CLBs are implemented using arrays of programmable logic gates, memory and other elements, such as DSPs.
FPGAs are indispensable parts of embedded electronic devices in several applications, such as cryptography, digital signal processing and Software Defined Radios (SDRs). There are also many commercial uses of FPGAs, such as Cisco routers and Amazon and Microsoft cloud service providers.
Why FPGA-based security?
FPGA-based security has some fundamental differences vs. security in processor-based systems. The major differences have to do with both the availability of information and the hardware systems control.
- Harder to hack what you don’t know
The processor’s internal hardware architecture is widely known in order for programmers to create the best-performing software. The availability of this information puts the processors at risk, as all the weaknesses and the ways for intrusion are given apriori to the attackers. On the other hand, FPGAs are less transparent than processors. FPGA systems have a well-documented high-level architecture, but lower-level details of the mapped design are left to the designer. Also, the scale of the design in modern FPGAs is huge, which makes reverse-engineering of the mapped systems’ details, practically impossible.
- FPGA-designers are in full-control of the system
Processors provide limited internal control to a programmer. On the other hand, an FPGA hardware designer has complete control over the logic that is used to map his/her design. In addition, the designer defines exactly the interfaces that will be used to connect his/her FPGA block with the rest of the system.
- System tampering
Tampering is always a concern for both hardware and software systems. A standard FPGA has its hardware committed and verified. Regardless of whether it’s inherently secure, an attacker is not able to tamper the FPGA hardware design due to its high complexity. Also, reverse engineering attacks to FPGA bitstreams is of high complexity as FPGA vendors do not have a standardized bitstream mapping for all FPGA devices.
- Information security
The FPGA security focuses on confidentiality, integrity, and authentication. FPGA designs map bitstreams, which are encrypted and prevent a competitor from stealing internal information. Also, FPGA bitstreams use data integrity checks to detect “accidental” modifications during chip loading. Last, the bitstream data transfer, during FPGA programming, is based always on an one-way communication channel with message authentication.
Concluding, FPGAs seem to be less flexible than software for workload mapping but, on the other hand, if the ultimate security is needed, FPGAs can offer higher levels than software. While nothing can eliminate completely the cybersecurity risk, the CYRENE FPGA-based security techniques introduce a fundamental shift in Supply Chain environments towards modern directions and offer truly resilient and secure systems reducing the attack surface.
FPGA and Snort
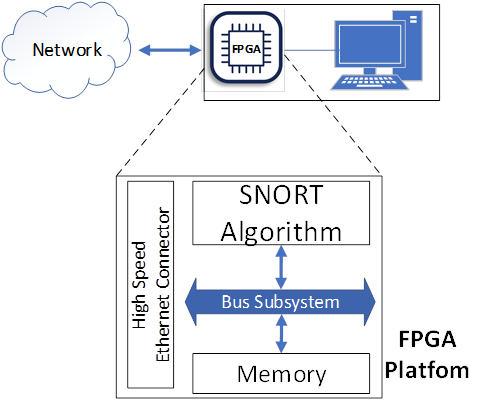
A cybersecurity solution that CYRENE framework offers is the pre-filtering of data exchange among Supply Chain nodes using FPGA devices that map an IDS algorithm, i.e., Snort algorithm. Snort is a widely-used and open-source Intrusion Detection and Prevention Framework (IDS/IPS) algorithm. The CYRENE FPGA-nodes map the Snort algorithm and offer high-speed cybersecurity incoming data filtering, setting free the Supply Chain nodes from cyber security issues/scans. The CYRENE FPGA-nodes are placed in front of the Supply Chain assets, as shown in the next Figure, and they will co-operate with other CYRENE based systems exchanging information and offering high-levels cyber security. More details about the CYRENE FPGA-based framework will be presented in the CYRENE blog during the next months.
So what do you think? Reach out to us and share your views either by using our contact form or by following our social media accounts in Twitter and LinkedIn.
Don’t forget to subscribe to our Newsletter for regular updates!
This blog is signed by: The TSI team
KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: info{at}cyrene.eu
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
