Supply Chain Vulnerability Assessment

Safeguarding the cybersecurity of supply chains (SCs) is an ever evolving and continuous challenge. As the supply chains become larger, more complex, and more unpredictable, this creates a plethora of cyber supply risks which demand a vigilant and dynamic approach to cybersecurity (ENISA, 2021).
In the context of the CYRENE project, we aim to tackle certain cybersecurity aspects related to the SCs. One of those aspects relates to the supply chain vulnerability assessment. A vulnerability assessment is the “search for potential weaknesses in the supply chain to prevent cyber threats“. It is a specialised form of cyber risk assessment. The task of detecting, identifying, and measuring the vulnerabilities located in the interconnected ICT components of SC services and systems is executed by the Dynamic Vulnerability Assessment Layer (DVAL) of the CYRENE platform. Towards revealing the presence of vulnerabilities in ICT-based SC services and systems, DVAL dynamically assesses the supply chain to discover vulnerability indicators (i.e., domain names, IP addresses, file hashes, or log indicators).
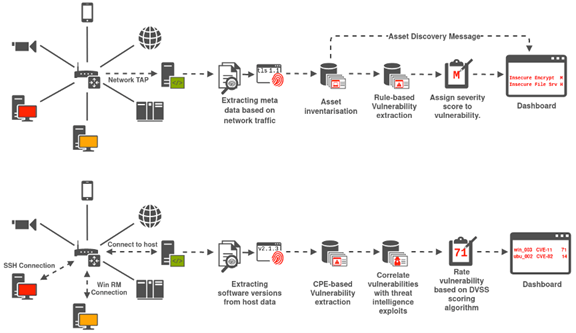
At its core, DVAL is comprised of several components which interact with each other to transform network data inputs and vulnerability indicators into actionable information presented to the CYRENE dashboard. As illustrated in Figure 1, DVAL can support two types of vulnerability analysis, namely passive and active scanning. the passive vulnerability analysis capabilities provided by DVAL are based on non-intrusive network data and meta-data analysis. DVAL ‘s passive vulnerability analysis can:
- Generate logs from observed network data collected via SPAN, TAP or streaming API interfaces.
- Extract key host-based indicators from specific logs that provide information regarding vulnerability protocols, services, or software.
DVAL also provides active vulnerability scanning capabilities. As part of the active vulnerability analysis, host-based indicators are collected in real-time, as they are observed on the network, and forwarded to an assessment engine to carry out the following activities:
- Check for corresponding Common Vulnerabilities and Exposures (CVEs) against vulnerability indicators. In case an identified vulnerability corresponds to a validated CVE or exploit, information will be extracted including a determined “impact” category.
- Cross-reference vulnerability indicators with active CVEs/exploits to quantify the identified vulnerability and provide vulnerability impact scoring using the Dynamic Vulnerability Scoring System (DVSS).
In both the active and passive modes, upon detection of a vulnerability, DVAL provides the security administrators with vulnerability alerts and early warnings empowering them to take actions to either acquire more information on the identified vulnerabilities, or to isolate the infected system(s) until a security mechanism is applied.
DVAL will be validated in the context of the CYRENE’s pilots. With the pilot trails beginning later this year, please stay tuned for updates and lessons learnt!
References:
European Union Agency for Cybersecurity (ENISA), Threat Landscape for Supply Chain Attacks, July 2021.
Online: https://www.enisa.europa.eu/publications/threat-landscape-for-supply-chain-attacks
So what do you think? Would your organization use the CYRENE DVAL? Reach out to us and share your views either by using our contact form or by following our social media accounts in Twitter and LinkedIn.
Don’t forget to subscribe to our Newsletter for regular updates!
This blog is signed by: Dr. Nikos Argyropoulos of the Exalens team
KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: info{at}cyrene.eu
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.