A Supply Chain (SC), in its simplest form, can be seen as the activities required by an organisation to deliver goods or services to the consumer. The management of a supply chain is the grasping of the entire production flow of a good or service — starting from the raw components all the way to delivering the final product to the consume.
Safeguarding the cybersecurity of a supply chain is not a simple exercise. NIST1 states that the cybersecurity in the supply chain cannot be viewed as an IT problem only, as cyber supply chain risks can affect sourcing, vendor management, supply chain continuity and quality, transportation security etc. Similarly, according to the latest ENISA report2, namely Threat Landscape for Supply Chain Attacks, which analysed 24 recent attacks, strong security protection is no longer enough for organisations when attackers have already shifted their attention to suppliers.
In the context of the CYRENE project, we aim to tackle several cybersecurity aspects related to the SCs through the development of a collaborative, multi-level evidence-driven Supply Chain Risk and Privacy Assessment Approach. This blogpost will focus on the privacy and data protection layer of CYRENE’s solution.
More specifically, this layer will enable Critical Information Infrastructures (CIIs) to set up security and data protection configurations based on existing legal and regulatory frameworks (such as the GDPR). This will allow them to incorporate the desired levels of data protection for sensitive information. The CYRENE approach will allow the application of the most appropriate security and data protection methods based on the organisation’s privacy requirements, in order to meet the highly demanding regulatory compliance obligations, for instance, in relation to accountability towards data protection supervisory authorities, for adequate management of informed consent.
To accomplish this, CYRENE will create a handbook that will incorporate the aforementioned and will allow application of the most appropriate security and data protection methods depending on organisation’s privacy requirements. This handbook will consider: (a) utilisation of privacy by design techniques, (b) development of methods that will contribute to the pseudonymisation of PIIs, (c) utilisation of well-known Privacy Enhancing Techniques (PETs), and (d) the development of a list of security and privacy controls of the organisation based on NIST and European Legislation.
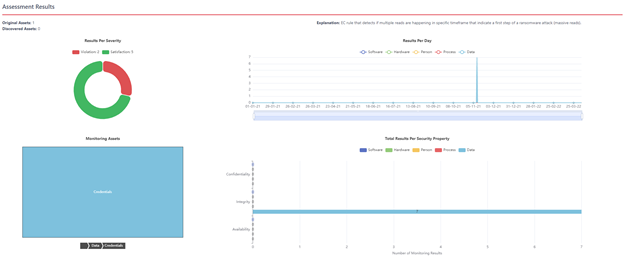
On top of that, CYRENE will utilise two components of Sphynx’s Security and Privacy Assurance Platform3 . The former, namely, EVEREST, is a runtime monitoring engine that will check if the organisations’ security and privacy controls are in place and well configured. The latter, namely Sphynx’s Event Captors, is a tool that, based on collected data and triggering events, formulates a rule or a set of rules and pushes the latter towards EVEREST for evaluation. Figure 1 presents the initial aggregated results of EVEREST’s deployment in a CYRENE environment.
EVEREST, and the Event Captors, will be validated in the context of the CYRENE’s pilots. With the pilot trials beginning later this year, please stay tuned for updates and lessons learnt!
So what do you think? Would your organization use the CYRENE with Sphynx’s Security and Privacy Assurance Platform? Reach out to us and share your views either by using our contact form or by following our social media accounts in Twitter and LinkedIn.
Don’t forget to subscribe to our Newsletter for regular updates!
This blog is signed by: Michalis Smyrlis of the Sphynx Technology Solutions AG team
KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: info{at}cyrene.eu
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.