The CYRENE framework focuses on introducing a fundamental shift in Supply Chain (SC) environments towards modern directions and offering truly resilient and secure systems reducing the attack surface. Based on that goal, solutions, and methodologies that support the detection of malicious activity over SCs are researched.
Security systems over SCs have to face three significant challenges:
- Complex supply chain networks and processes.
The significant complexity of SC infrastructures, coupled with the corresponding SC operations, technologies, and mechanisms, poses critical performance requirements, where all the processes strive toward complete automation, i.e. ENISA’s (European Union Agency for Cybersecurity) directions [1]. - Cybersecurity workloads with high processing demanding.
Most of the monitoring and intrusion detection systems require a relatively long time to process incoming streams of network packets. - Continuous and dynamic update of the cybersecurity systems.
The existing SC security systems offer threat prevention and mitigation techniques based on static network intrusion detection rules [2]. On the other hand, they need to defend SCs from continuously new security issues with new and dynamic rules [3],[4]
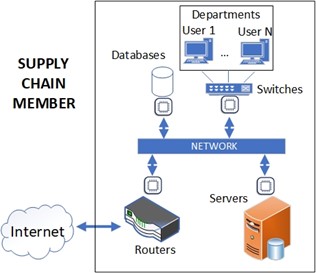
Based on the above challenges the CYRENE framework introduces a high-end IDS solution for supply chains that completely disentangles the supply chain assets from cybersecurity workloads while supporting dynamic updating of the security features [5]. The CYRENE IDS solution resides on a high-end, low-cost, and low-resources reconfigurable node, which can be easily installed into complex supply chain infrastructures. The IDS nodes are integrated into a supply chain structure and they are placed as intermediate nodes between the assets’ incoming network connection and the supply chain assets, Figure 1. This solution covers the supply chain structure from both the external (i.e., external network connection) and the internal (i.e., other supply chain components) cybersecurity threats.
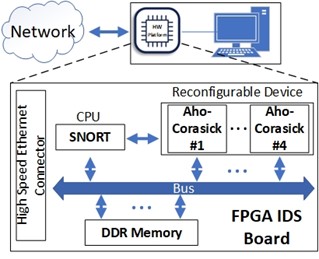
In more details, each node maps the official Snort IDS security mechanism while accelerating it using the parallel process that FPGA integrated devices offer. Specifically, the Snort algorithm runs on an integrated Arm Cortex A4 CPU. The algorithm collects the network data packets (i.e., Ethernet network packets) and stores them into the FPGA DDR memory. Subsequently, the reconfigurable device reads the incoming packets and processes them in-parallel in modules that implement the Aho-Corasick algorithm, i.e., four parallel independent memory ports between the reconfigurable device and the CPU. The results from the Aho–Corasick modules are stored back to the DDR and they are retrieved by the Arm-based Snort. If there is an intrusion alert, a message with the corresponding information is passed through Ethernet to the supply chain server. The final implemented design on the FPGA-based IDS node is presented in Figure 2.
The CYRENE IDS system advances the cybersecurity capabilities of supply chains in a range of different ways. First, it offers real-time cyber-threat monitoring and intrusion detection over complex supply chain infrastructures, i.e., IDS workload acceleration about six times over the best optimized software solutions. Second, the proposed module offloads completely the highly demanding cybersecurity workloads from the supply chain components, leading to optimized supply chain infrastructures. Third, the proposed lightweight and dedicated hardware for security purposes reduces the overall size of the framework resources and, subsequently, their cost, i.e. it suppresses the cost of supply chain servers that are responsible for the intrusion detection process. Finally, the proposed solution takes advantage of one of the main characteristics of reconfigurable-based platforms, i.e., low-energy consumption. The CYRENE system offers a crucial reduction in energy consumption, i.e., the proposed system offers up to almost 12x lower energy consumption vs. a modern high-end single-socket server!
References
[1] ENISA—European Union Agency for Cybersecurity. Available online: https://www.enisa.europa.eu/
[2] Solarwinds Supply Chain Attack. Available online: https://blog.securityonion.net/2020/12/solarwinds-supply-chain-attack.html.
[3] ENISA Threat Landscape For Supply Chain Attacks. 2021. Available online: https://www.enisa.europa.eu/publications/threat-landscape-for-supply-chain-attacks
[4] Snort Rule Update. 2021. Available online: https://blog.snort.org/2021/07/snort-rule-update-for-july-6-2021.html
[5] “Deyannis, D., Papadogiannaki, E., Chrysos, G., Georgopoulos, K., & Ioannidis, S. (2022). The Diversification and Enhancement of an IDS Scheme for the Cybersecurity Needs of Modern Supply Chains. Electronics, 11(13), 1944.
So what do you think? Does your organisation need an Intrusion Detection System?
Reach out to us and share your views either by using our contact form or by following our social media accounts on Twitter and LinkedIn.
Don’t forget to subscribe to our Newsletter for regular updates!
This blog is signed by: the TSI team
KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: info{at}cyrene.eu
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.