This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
1st CYRENE Workshop presentations

Workshop Agenda
Time | Topic | Speaker |
10:00-10:05 | Welcome | Farhan Sahito |
10:05-10:20 | Sofoklis Efremidis Sophia Karageorgou | |
10:20-10:30 | Haris Mouratidis | |
10:30-10:50 | Supply Chains (SC) as Targets of Evaluation (ToE), CYRENE ToEs | Alexandra Michota Elma Kalogeraki |
10:50-11:10 | Danijela Boberic | |
11:10-11:40 | CYRENE Questionnaire Feedback, discussion, Q/A by AB members Collection of end user requirements | Danijela Boberic Sofoklis Efremidis |
11:40-11:45 | Conclusions and closing remarks | Farhan Sahito |
Intro











CYRENE Overview
Our Technical Approach



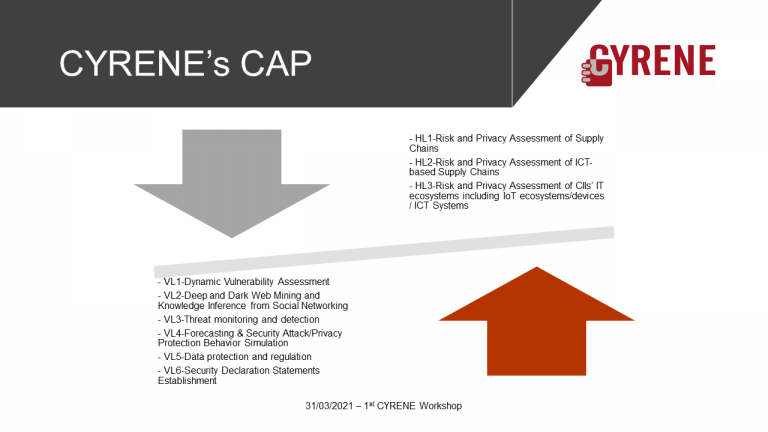


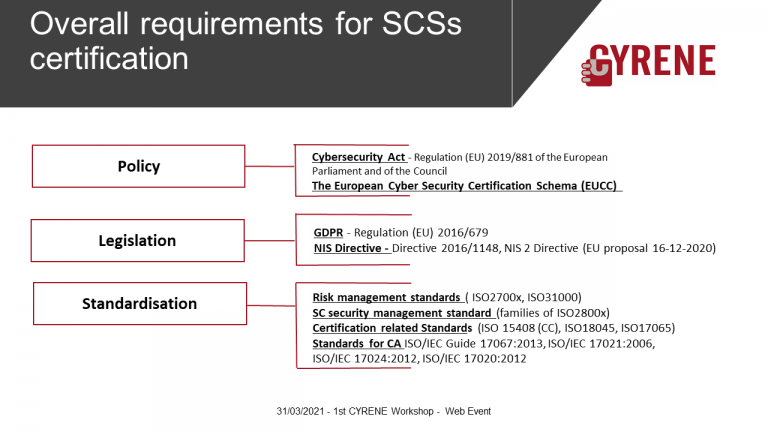
Security of Supply Chain Services

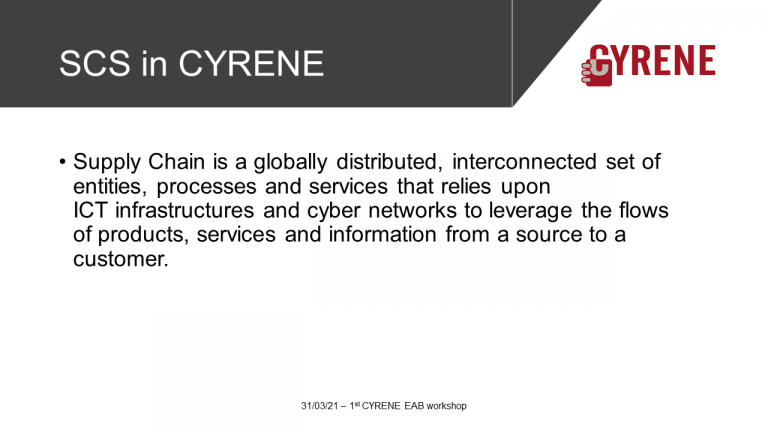
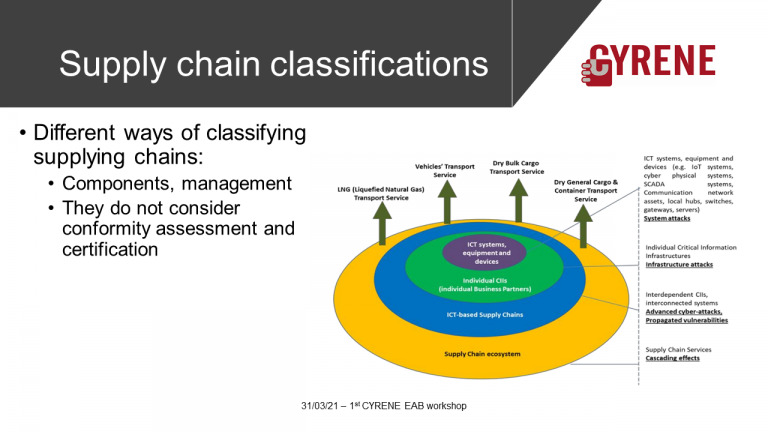
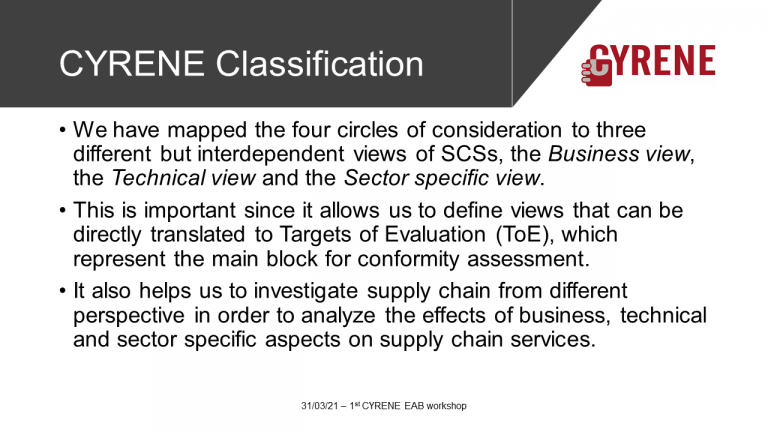
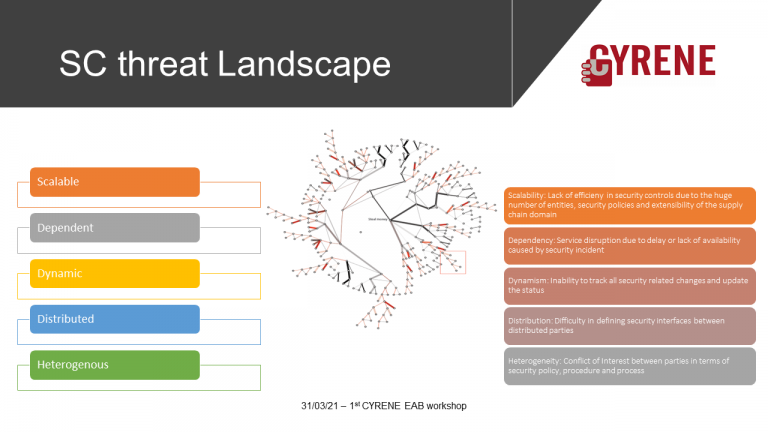
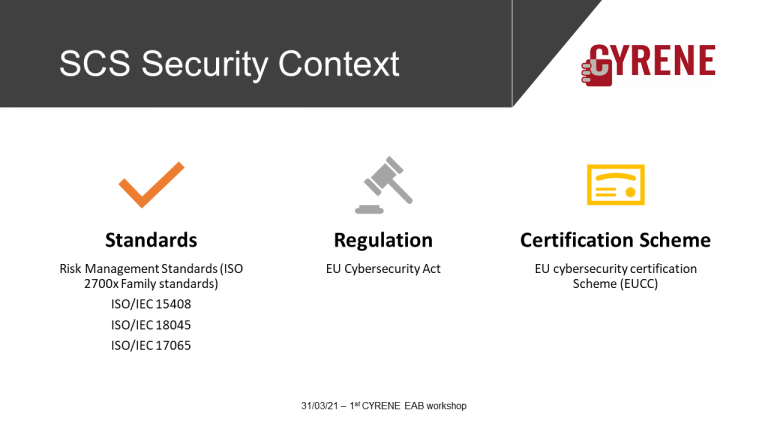

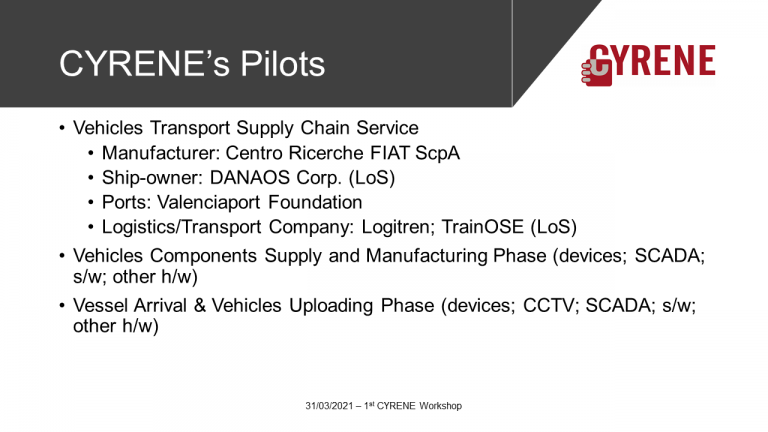
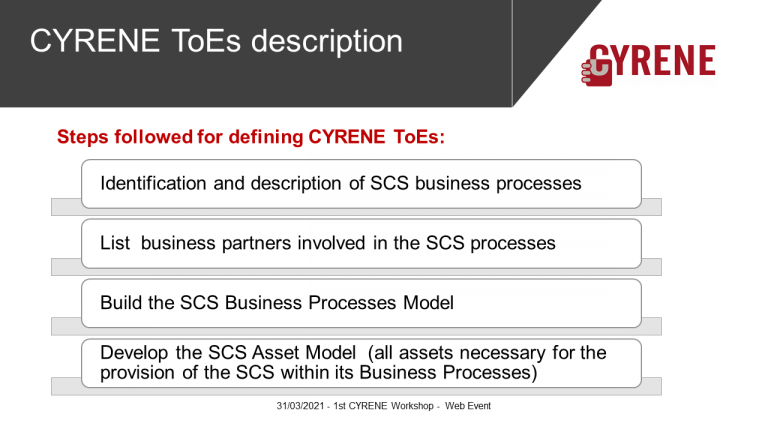
Supply Chain Services (SCS ) as Targets of Evaluation (ToE)






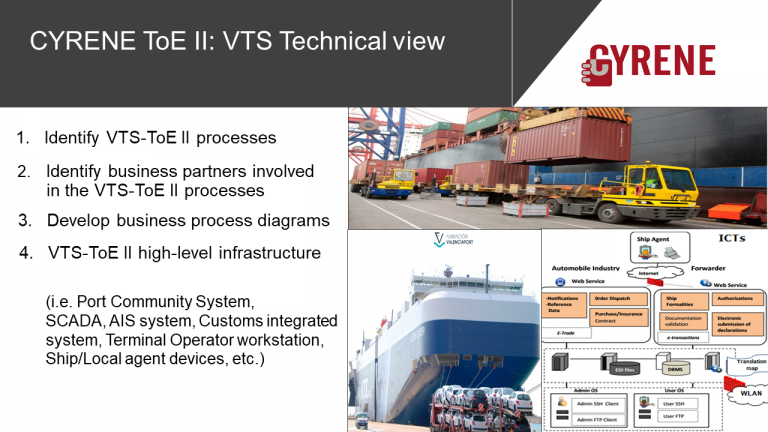



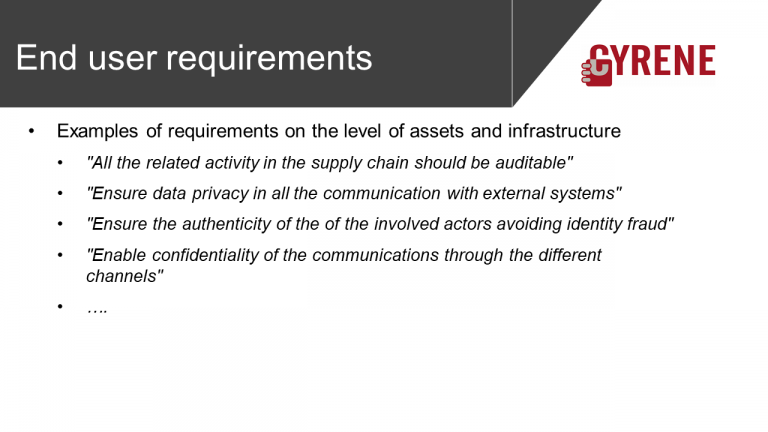
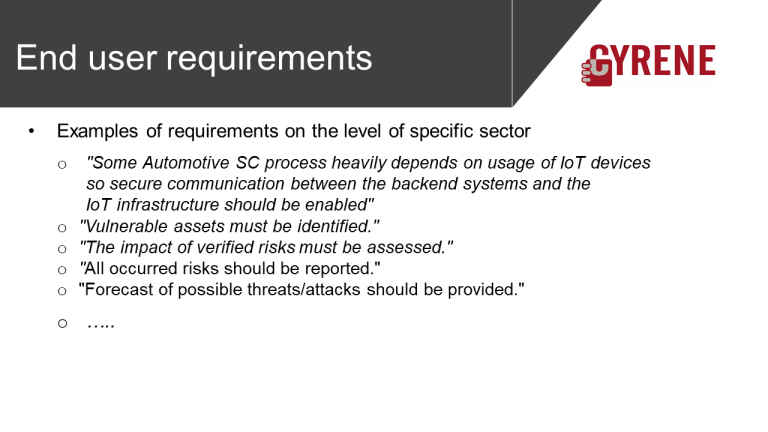
End user requirements




KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: sofoklis.efremidis@maggioli.gr
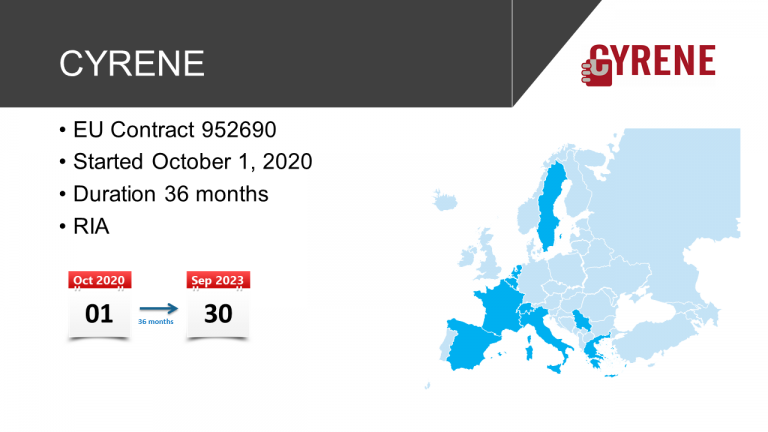
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.

