The formal quantification of cyber risk, and therefore, the prioritization of controls’ enforcement in every organization is of high importance due to the heterogeneity and a large number of interconnected assets (i.e., wireless devices, cloud services, enterprise or governmental applications). The complexity is getting higher when considering the case of interconnected assets that are exposed via Application Programming Interfaces (APIs) and services across different and multiple organizations as part of a supply chain. The modeling of assets in the interconnected supply chains and the calculation of the risk level among different businesses with variable and domain-specific criticality, software, and hardware products are both challenging and constantly increasing in these diverse application contexts. However, existing risk assessment methods do not consider the cyber-dependencies of such interconnected assets across different organizations, their temporal and environmental (i.e., systemic) characteristics, or other aspects related to the data, facilities, and people. The research focus in the CYRENE project takes into account the network dependencies, the data flows (i.e., exposed APIs or services), facilities and people, temporal and environmental characteristics.
The Risk and Conformity Assessment component of CYRENE reframes the calculation of cyber risk and the impact assessment. It further enhances Confidentiality, Integrity, and Availability (CIA) through actionable reports in heterogeneous supply chain services. In CYRENE, we deliver a software solution that collects and combines Vulnerabilities, Weaknesses, and Attack Patterns from well-known open data sources to comply with their schema. The software adopts the well-known schemas in the backend services for interoperability and reusability, and as an outcome it makes threat sharing more effective. All the collected and harmonized information is linked with the cyber assets, takes into account dependencies among the exposed services and connected systems, and enables a continuous risk management process that can further trigger controls at runtime. The software solution considers both the temporal and environmental/systemic dependencies to discover attack paths in interconnected supply chain services. This means that in a formal and dependency-based risk analysis, the neighboring cyber assets with direct connections, as well as the non-adjacent assets which may logically influence a target asset, are all taken into consideration due to their functional dependency.
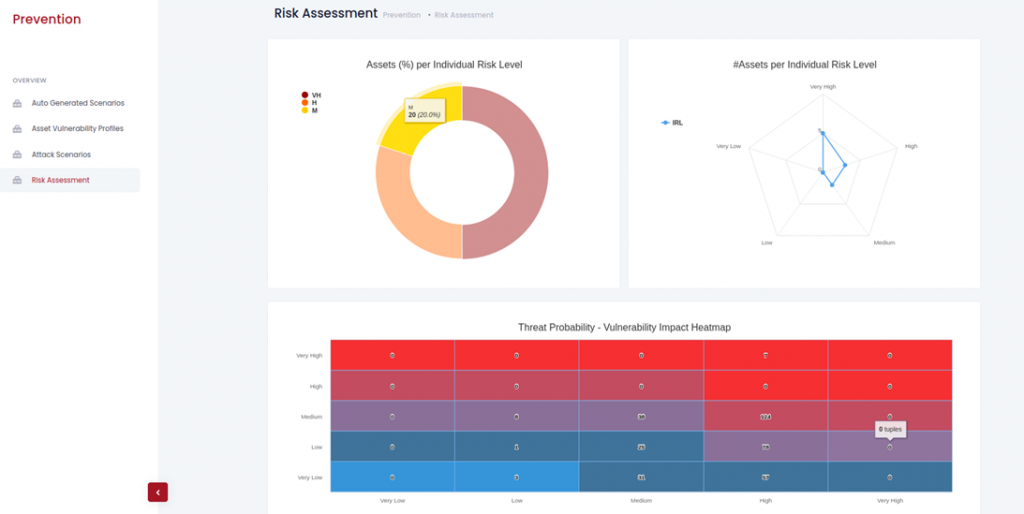
The overview report, as illustrated in Figure 1, depicts the individual risk per asset and the heatmap of threat probability vs. vulnerability impact adopting the coloring pattern from blue to red which expresses the escalation of the impact from very low to very high. We highlight the advantages of combining formal analysis, verification, and calculations with actionable visualizations and reports when used to assess cybersecurity risks in such complex application contexts. Task Force (IETF).
KEY FACTS
Project Coordinator: Sofoklis Efremidis
Institution: Maggioli SPA
Email: info{at}cyrene.eu
Start: 1-10-2020
Duration: 36 months
Participating organisations: 14
Number of countries: 10
FUNDING
 This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.
This project has received funding from the European Union’s Horizon 2020 Research and Innovation program under grant agreement No 952690. The website reflects only the view of the author(s) and the Commission is not responsible for any use that may be made of the information it contains.